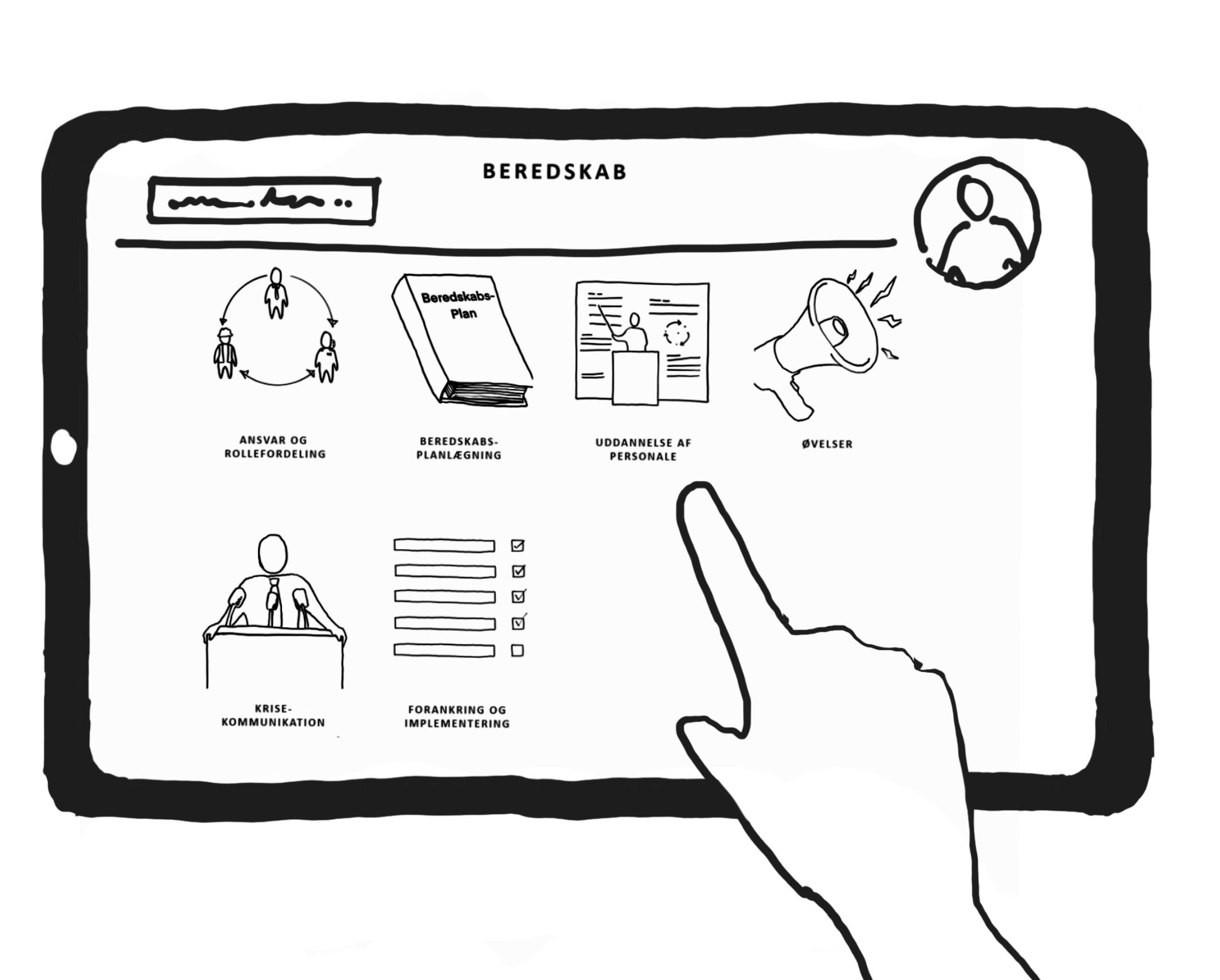
Risikoværktøj
Hvad skal risikoanalysen dække over?
Public Sites: This category is for people who want to identify protective security needs in e.g. pedestrian areas, public squares, parks and attractions. If the risk assessment is based on an outdoor event, you should select the category Event.
Building: This category is for people who want to identify protective security needs at, e.g. office, cultural, religious and political buildings, institutions, and sports arenas. If you are planning an event in a building, you should choose the category Event.
Event: This category is for people who want to identify protective security needs for events. This is for temporary indoor and outdoor events. If it regards a building that is to be used permanently for events (e.g. assembly halls, concert venues, etc.), you should choose the Building category. If you are working with a public outdoor area that can be used for events (e.g. waterfront, park area, city square), you should choose the category Public Sites.
Aktiver
The assessment of assets is a crucial part of the overall assessment, as it helps you decide whether you have assets worth protecting and, therefore, whether a potential perpetrator will find your site attractive.
In the list below, some assets are autogenerated, depending on your previous selection of category. The assets are a suggestion, so you should consider whether they fit your context. You also have the option to add assets that are specific to your location; this may be a specific material asset, important person or function critical to society.
First, you should consider which assets are valuable to you. This includes assets you may have to protect (people, critical infrastructure, targets of symbolic importance, etc.), high-value assets (e.g. cash, jewellery, art), and unique assets that are difficult to replace or reacquire.
Next, consider assets that are essential to your work. This typically includes equipment, utilities, transportation and information systems vital to operations. The essential assets can also be outlying departments located away from the head office, which, if lost, stop the rest of the organisation's operations.
Assets should be valued from 1-10. The more valuable and/or essential you think the categories are to you, the higher value they should be assigned.
Aktiver
Værdier































Trusselsvurdering
Terrorism in the West are most often associated with one of three forms of violent extremism: extreme Islamism, extreme right politics and extreme left politics. The Danish Centre for Prevention of Extremism defines extremism as follows:
Extremism refers to individuals or groups who commit or seek to legitimise violence or other unlawful acts in reference to social conditions with which they are dissatisfied.
The purpose of the threat assessment is to clarify whether your location is a potential attractive terrorist target. Both soft targets – people or crowded places with low security and high accessibility e.g. schools, shopping centres, and public transport – and hard targets e.g. things or buildings, where public access is limited and security is often higher, can be attractive terrorist targets. An attacker will typically aim to harm a large number of people or a target of symbolic importance to gain as much media coverage as possible. However, there have also been cases where the attacks have targeted individuals chosen explicitly by the attacker.
In their "Assessment of the terrorist threat against Denmark (2024)" The Danish Security and Intelligence Service (DSIS) describes the terrorist threat in Denmark in the following way:
“It is the overall assessment of CTA that the terrorist threat to Denmark remains at the level of significant.”
In Denmark and the rest of the world, there have been both thwarted and successful aimed at organisations, crowds, and individuals. The attacks have occurred both in the public domain and at private addresses.
Arrangement
Does your location fit into one of the following categories?
Is the event situated in a larger urban area?
In this context, a larger urban area is defined as either the metropolitan area of a country’s capital city, typically encompassing the central city and its closely linked suburbs. Additionally, other major cities in the country, which are significant urban centers that play key roles in regional or national life.
Are there assets at the event that can be perceived as having symbolic value?
Symbolic value includes e.g. certain population segments (religious and political), cultural assets, and crowded places.
Are there any obviously attractive terrorism targets near the event?
Obvious targets include symbolic targets (religious or political) or crowded places e.g. pedestrian pathways, festivals, public squares, and tourist attractions.
Will there be many people with high density at the event?
High density is defined as more than 2 people per square meter e.g. at gatherings or events without table arrangements. Peak periods refer to the busiest time of day with the highest number of people at the location.
Is there valuable cultural and natural heritage at the event?
Cultural and natural heritage encompasses cultural and natural historical areas, such as UNESCO World Heritage sites, museums, and protected nature. An attack against cultural and natural heritage can contribute to generating media coverage, as well as damaging irreplaceable assets.
Is the event and/or participants generally known and the subject of media coverage?
Some events may be widely known due to their popularity or by being a recurring event, such as major festivals, parades or sporting events. Participants often mentioned in the media e.g. musicians, actors, artists and other celebrities, sports stars, royalty, and religious leaders.
Is the event easily accessible to an attacker?
Events that are easily accessible have no entry controls. E.g. no physical barriers, electronic surveillance, user/visitor registration or security checks such as bag or body searches. Maybe due to the event having free admission.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Perimeter og sikkerhedszone
Perimeteren er den ydre grænseflade af et areal eller en grund, der ofte støder op til nabogrund eller offentligt rum.
Området mellem perimeteren og skallen af bygningen kan anvendes som en sikkerhedszone, der kan forsinke, mindske eller modstå konsekvenserne af en potentiel hændelse.
Is the site/event's perimeter protected with mechanical security measures?
Perimeter refers to the outer boundary of your property, which can be simply marked or alternatively, physically protected with features such as a fence or wall.
Is there vehicle access control at the site/event's perimeter?
Access to the area is actively monitored and physically controlled, to prevent vehicles from having unrestricted access.
Is the site/event's perimeter monitored with electronic security measures?
Perimeter refers to the boundary of your property/event, which you can choose to monitor with e.g. CCTV surveillance.
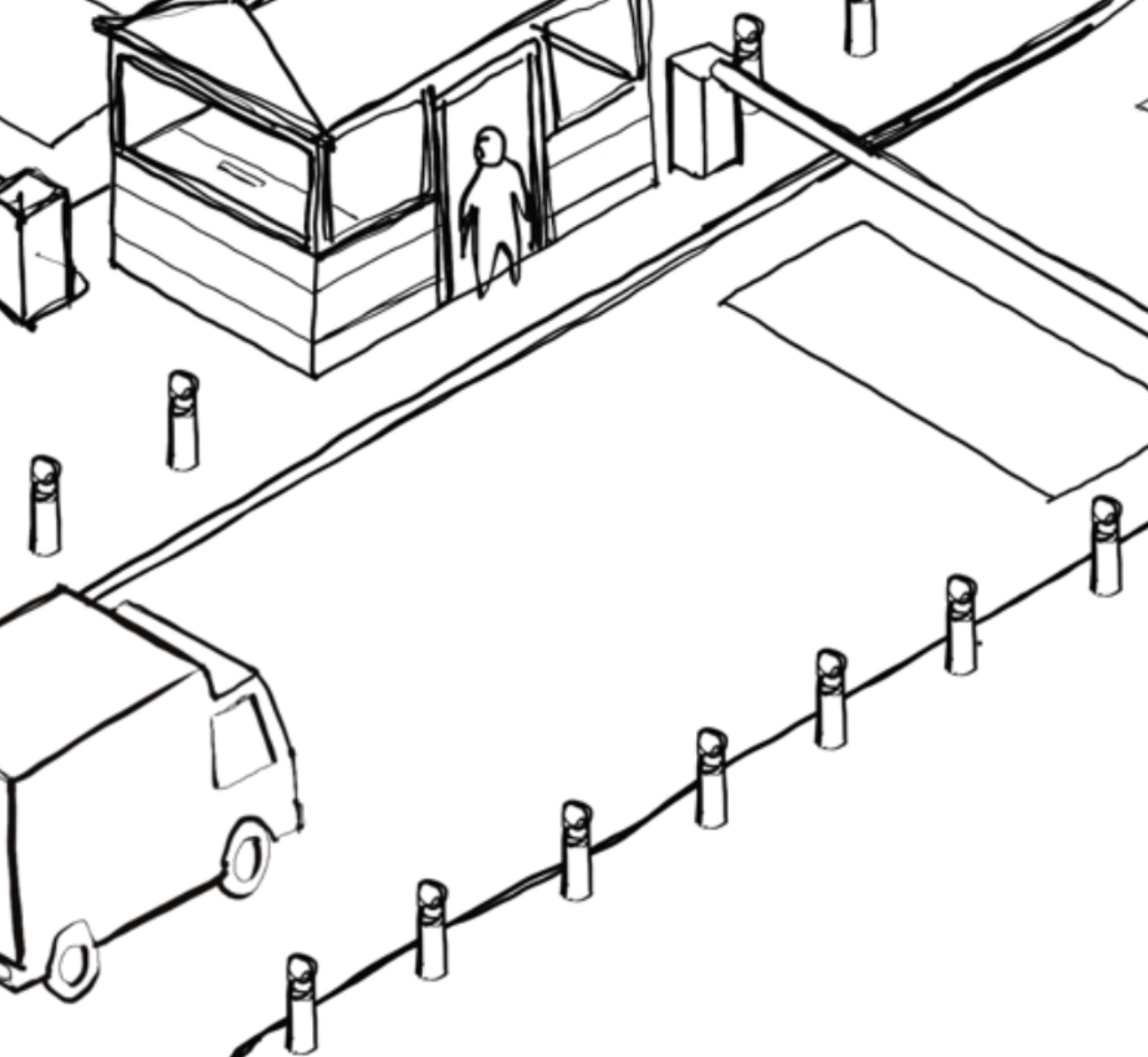
Have HVM-measures been installed in the site/event's perimeter?
Hostile Vehicle Mitigation measures, restricting vehicle access and impact include but are not limited to bollards, wedges, reinforced street furniture, trees, or sculptures.
Are the HVM measures certified, or have tests to document the resistance strength been completed?
With a Vehicle Dynamics Assessment (VDA), one can test the resistance strength of e.g. a sculpture or a bench against the specific type of vehicle one wants to protect against.
Can vehicles reach high speed when approaching the site/event?
High speed can be achieved if there is a long, straight stretch without obstacles, leading to the site. Curbs, ditches, or vegetation can reduce vehicle speed and as a result, any collision impact.
Can there be significant crowd or queue build-up near the entrance to the site/event?
Larger crowds or queues can occur if the site/event is used for events. If populations gather outside the site/event without Hostile Vehicle Mitigation measures, it increases the risk of a vehicle attack.
Is there a distance between the site/event and the perimeter/public space?
The distance between a perimeter and the building affords the possibility to install additional security measures and can reduce the effect of a potential attack.
Is the site/event illuminated?
This refers to external artificial lighting.
Are there visible signs that clearly indicate restricted access to the site/event and/or implemented security measures?
For example, CCTV surveillance.
Is the site/event protected by security guards?
Patrolling guards perform dynamic tasks of various kinds, at different times and by different routes in all or parts of the building, as well as grounds. Static guards are stationed at a fixed location and often perform tasks related to regular routines. Mobile patrols mostly use vehicles to patrol multiple locations and are often called upon as needed.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Skal, Sektion og Celle
Skallen er en bygnings ydre grænseflade – ofte ydermuren.
Selve bygningen kan sektionsopdeles, så sektionerne sikres med forskellige sikkerhedsniveauer.
Bygningsceller er ofte mindre lokaler i en bygning, der er særskilt sikret.
Is the site/event monitored with electronic security measures?
Electronic security measures refer to surveillance and monitoring equipment such as closed circuit television (CCTV), intrusion detection system (IDS), access control system (ACS) etc.
Is there access control at the entrance(s) to the site/event?
Access control covers refers to registration, restriction, security checks, and monitoring. E.g. unlocking using key/electronic access medium, guest list or ticket control, reception registration, bag and body checks, guards, etc. Users include both staff and guests.
Can a person access the site/event through alternative passages or supply routes?
Alternative passages or supply routes encompass all other entrances besides doors and windows, which may include e.g. loading docks, sewer systems, water drainage, or other corridors.
Is the event's air supply and ventilation secured?
An attack with dangerous substances and materials can exploit unprotected airsupply and ventilation channels. These can be monitored and protected with e.g. filters and designed so tools are required to gain access.
Is the site/event's utilities supply secured against interruptions, throughout the entire duration of the event?
Supply refers to essentials such as electricity, gas, internet, and telecommunications that are necessary to maintain operations or crucial functions e.g. security systems. Secured supply implies the establishment of emergency supply or protective security measures.
Can the site/event's critical assets be observed from street level or adjacent buildings?
Critical assets refer to e.g. employees and symbolic targets whos protection is a priority.
Are there internal security layers through separately secured sections and/or cells?
An internal division of the building into sections or cells that are individually secured, typically to a higher level of security. E.g. through mechanical keys, multiple factor authentification for the access control, reinforced walls, higher grade doors, or with guards.
Have protected spaces/ access routes that can withstand prolonged intrusion attempts been established in the building/event?
Protected spaces/ access routes such as a safe room, should be designed according to a specific risk assessment.The resistance class (RC) defines the resistance time against intrusion according to a specified standard.
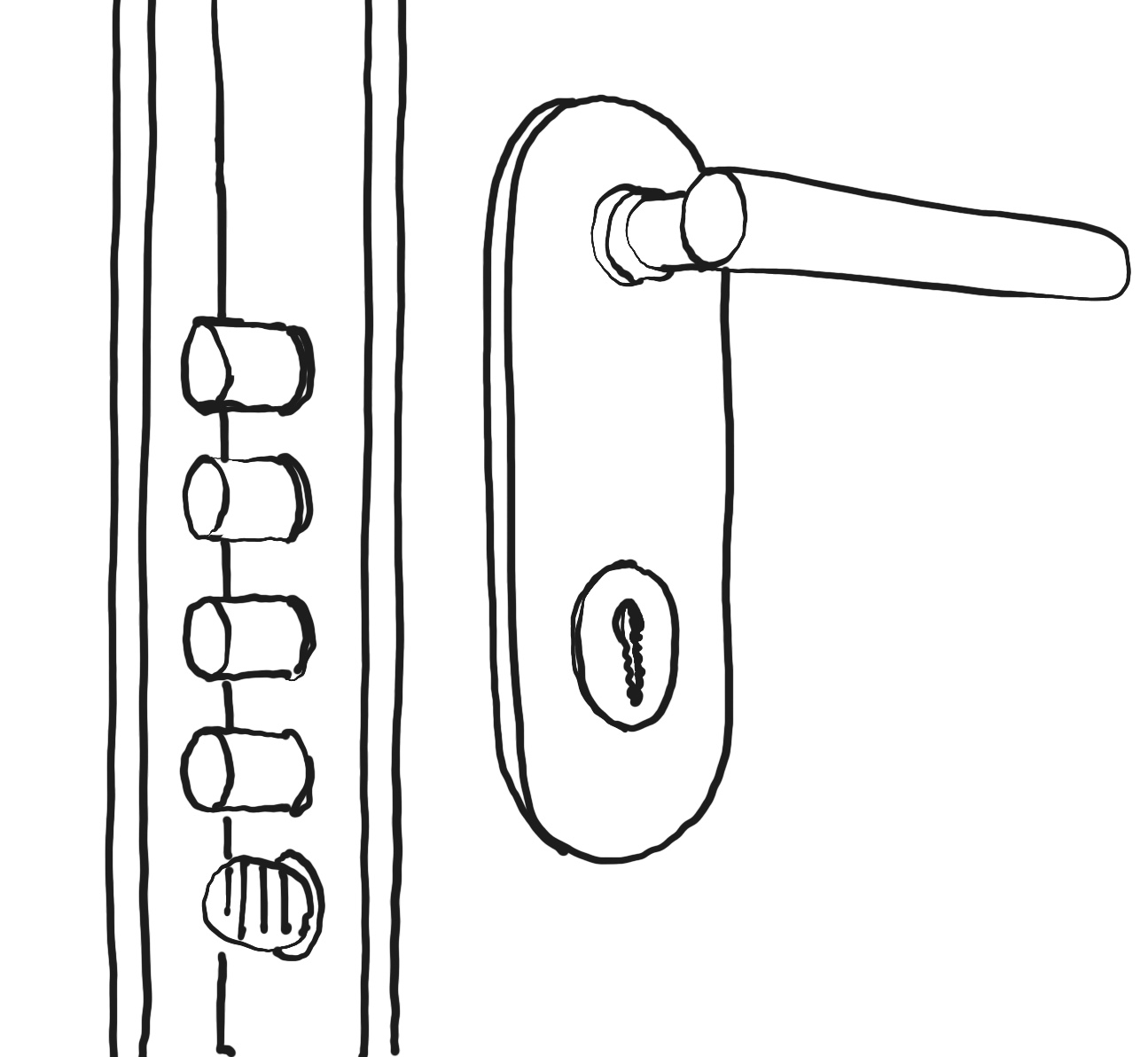
Are the building/event's doors, windows, and glass facades reinforced with e.g. security doors and glass, security film, etc.?
Ballistic attacks refer to the use of firearms.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Sikkerhedskultur
Sikkerhedskultur handler om, hvordan organisationen og medarbejderne opfatter og behandler risici og ulykker/hændelser. Der findes både gode og dårlige eksempler på sikkerhedskultur, men i alle tilfælde bør organisationer bestræbe sig på at opnå en god og styrket sikkerhedskultur, hvor medarbejderne føler, at det er sikkert at gå på arbejde hver dag.
Do you have security procedures for the identification and validation of external persons accessing the site/event?
External persons include but are not limited to e.g. delivery personnel bringing food, flowers, and mail/packages, suppliers, visiting guests or customers, or contractors.
Do you have security procedures for recruitment?
Background checks can vary in scope, according to your needs and national legislation. The point is to verify that the person is who they claim to be and qualify their character.
Har I en procedure til identificering og håndtering af mistænkelige objekter?
Efterladte genstande som f.eks. tasker og pakker der gør sig bemærket ved deres tilstedeværelse.
Is there a focus on safety and security culture within the organisation?
How the organisation and its employees perceive and address safety and security risks and topics such as risk perception, awareness, and information security.
Is there a security and emergency management plan in place?
In the planning process, efforts are made to prevent and handle incidents.This means that through education, training, and planning, one enhances the ability to handle incidents that could threaten the site/event and its critical assets.
Have you conducted emergency drills before the event?
E.g. an evacuation drill designed to test the existing plan and see if it functions as intended.
Is there a crisis management function in place, including roles and responsibilities?
When an incident escalates to a point where the emergency management plan no longer suffice, it transitions to crisis management.
Trusselsvurdering
Terrorism in the West are most often associated with one of three forms of violent extremism: extreme Islamism, extreme right politics and extreme left politics. The Danish Centre for Prevention of Extremism defines extremism as follows:
Extremism refers to individuals or groups who commit or seek to legitimise violence or other unlawful acts in reference to social conditions with which they are dissatisfied.
The purpose of the threat assessment is to clarify whether your location is a potential attractive terrorist target. Both soft targets – people or crowded places with low security and high accessibility e.g. schools, shopping centres, and public transport – and hard targets e.g. things or buildings, where public access is limited and security is often higher, can be attractive terrorist targets. An attacker will typically aim to harm a large number of people or a target of symbolic importance to gain as much media coverage as possible. However, there have also been cases where the attacks have targeted individuals chosen explicitly by the attacker.
In their "Assessment of the terrorist threat against Denmark (2024)" The Danish Security and Intelligence Service (DSIS) describes the terrorist threat in Denmark in the following way:
“It is the overall assessment of CTA that the terrorist threat to Denmark remains at the level of significant.”
In Denmark and the rest of the world, there have been both thwarted and successful aimed at organisations, crowds, and individuals. The attacks have occurred both in the public domain and at private addresses.
Bygninger
Does your location fit into one of the following categories?
Is the location situated in a larger urban area?
In this context, a larger urban area is defined as either the metropolitan area of a country’s capital city, typically encompassing the central city and its closely linked suburbs. Additionally, other major cities in the country, which are significant urban centers that play key roles in regional or national life.
Are there assets at the location that can be perceived as having symbolic value?
Symbolic value includes e.g. certain population segments (religious and political), cultural assets, and crowded places
Are there any obviously attractive terrorism targets near the location?
Obvious targets include symbolic targets (religious or political) or crowded places e.g. pedestrian pathways, festivals, public squares, and tourist attractions.
Is there often a high number of people in the building?
Peak periods refer to the busiest time of day with the highest number of people at the location.
Is there valuable cultural and/or natural heritage at the location?
Cultural and natural heritage encompasses cultural and natural historical tangible or intangible assets, such as artefacts, UNESCO World Heritage sites, museum pieces, and protected nature. An attack against cultural and natural heritage can contribute to generating media coverage, as well as damaging irreplaceable assets.
Is the building and/or its occupants generally well-known and the subject of media coverage?
Generally well-known buildings include, but are not limited to, certain local businesses, arenas, assembly places, cultural establishments and popular hospitality venues. Some buildings may be the subject of media coverage due to the occupants, such as celebrities, royalty, and religious leaders.
Is the building easily accessible to an attacker?
Buildings that are easily accessible have no entry controls. E.g. no physical barriers, electronic surveillance, user/visitor registration or security checks. This may be due to the building's function or the decision to opt out of security solutions.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Perimeter og sikkerhedszone
Perimeteren er den ydre grænseflade af et areal eller en grund, der ofte støder op til nabogrund eller offentligt rum.
Området mellem perimeteren og skallen af bygningen kan anvendes som en sikkerhedszone, der kan forsinke, mindske eller modstå konsekvenserne af en potentiel hændelse.
Is the site/building's perimeter protected with mechanical security measures?
Perimeter refers to the outer boundary of your property, which can be simply marked or alternatively, physically protected with features such as a fence or wall.
Is there vehicle access control at the site/building's perimeter?
Access to the area is actively monitored and physically controlled, to prevent vehicles from having unrestricted access.
Is the site/building's perimeter monitored with electronic security measures?
Perimeter refers to the outer boundary of your property, which you can choose to monitor with e.g. CCTV surveillance.
Have HVM-measures been installed in the site/building's perimeter?
Hostile Vehicle Mitigation measures, restricting vehicle access and impact include but are not limited to bollards, wedges, reinforced street furniture, trees, or sculptures.
Are the HVM measures certified, or have tests to document the resistance strength been completed?
With a Vehicle Dynamics Assessment (VDA), one can test the resistance strength of e.g. a sculpture or a bench against the specific type of vehicle one wants to protect against.
Is there a distance between the building and the perimeter?
The distance between a perimeter and the building affords the possibility to install additional security measures and can reduce the effect of a potential attack.
Is the area outside the building illuminated?
This refers to external artificial lighting.
Are there visible signs that clearly indicate restricted access to the building and/or implemented security measures?
For example, CCTV surveillance.
Is the building protected by security guards?
Patrolling guards perform dynamic tasks of various kinds, at different times and by different routes in all or parts of the building, as well as grounds. Static guards are stationed at a fixed location and often perform tasks related to regular routines. Mobile patrols mostly use vehicles to patrol multiple locations and are often called upon as needed.
Can vehicles reach high speed when approaching the site/building?
High speed can be achieved if there is a long, straight stretch without obstacles, leading to the site. Curbs, ditches, or vegetation can reduce vehicle speed and as a result, any collision impact.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Skal, Sektion og Celle
Skallen er en bygnings ydre grænseflade – ofte ydermuren.
Selve bygningen kan sektionsopdeles, så sektionerne sikres med forskellige sikkerhedsniveauer.
Bygningsceller er ofte mindre lokaler i en bygning, der er særskilt sikret.
Is the building externally monitored with electronic security measures?
Electronic security measures refer to surveillance and monitoring equipment such as closed circuit television (CCTV), intrusion detection system (IDS), access control system (ACS) etc.
Are the building's doors, windows, and glass facades reinforced with e.g. security doors and glass, security film, etc.?
Ballistic attacks refer to the use of firearms.
Is there access control at the entrance(s) to the building for all users?
Access control covers refers to registration, restriction, security checks, and monitoring. E.g. unlocking using key/electronic access medium, guest list or ticket control, reception registration, bag and body checks, guards, etc. Users include both staff and guests.
Can a person access the building through alternative passages or supply routes?
Alternative passages or supply routes encompass all other entrances besides doors and windows, which may include e.g. loading docks, sewer systems, water drainage, or other corridors.
Is the building's air supply and ventilation secured?
An attack with dangerous substances and materials can exploit unprotected airsupply and ventilation channels. These can be monitored and protected with e.g. filters and designed so tools are required to gain access.
Is the building's utilities supply secured against interruptions?
Supply refers to essentials such as electricity, gas, internet, and telecommunications that are necessary to maintain operations or crucial functions e.g. security systems. Secured supply implies the establishment of emergency supply or protective security measures.
Can the building's critical assets be observed from street level or adjacent buildings?
Critical assets refer to e.g. employees and symbolic targets whos protection is a priority.
Are there internal security layers through separately secured sections and/or cells?
An internal division of the building into sections or cells that are individually secured, typically to a higher level of security. E.g. through mechanical keys, multiple factor authentification for the access control, reinforced walls, higher grade doors, or with guards.
Have protected spaces/ access routes that can withstand prolonged intrusion attempts been established in the building?
Protected spaces/ access routes such as a safe room, should be designed according to a specific risk assessment.The resistance class (RC) defines the resistance time against intrusion according to a specified standard.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Sikkerhedskultur
Sikkerhedskultur handler om, hvordan organisationen og medarbejderne opfatter og behandler risici og ulykker/hændelser. Der findes både gode og dårlige eksempler på sikkerhedskultur, men i alle tilfælde bør organisationer bestræbe sig på at opnå en god og styrket sikkerhedskultur, hvor medarbejderne føler, at det er sikkert at gå på arbejde hver dag.
Do you have security procedures for receiving, screening, and opening mail/packages?
This refers to where, when, and how mail and packages are received, distributed internally, and opened.
Do you have security procedures for the identification and validation of external persons accessing the building?
External persons include but are not limited to e.g. delivery personnel bringing food, flowers, and mail/packages, suppliers, visiting guests or customers, or contractors.
Har I sikkerhedsprocedurer til rekruttering?
Baggrundscheck kan variere i omfang, men her menes der som minimum at man har modtaget en straffeattest og fulgt op på mindst tre referencer.
Do you have a procedure for the identification and handling of suspicious objects?
Unattended objects such as bags and packages that draw attention due to their presence.
Is there a focus on safety and security culture within the organisation?
How the organisation and its employees perceive and address safety and security risks and topics such as risk perception, awareness, and information security.
Is there work being done on emergency management planning, and is there an emergency management plan in place?
In emergency management planning, efforts are made e.g. to prevent incidents that go beyond the day-to-day operations. This means that through education, training, and planning, one enhances ability to handle incidents that could threaten the organisation's assets and critical processes.
Are the building's escape routes clear and known to the building's daily users?
Individuals who use the building daily including staff and service personnel.
Do you conduct emergency drills?
E.g. an evacuation drill designed to test the existing plan and see if it functions as intended.
Is there a crisis management function in place, including roles and responsibilities?
When an incident escalates to a point where the emergency management plan no longer suffice, it transitions to crisis management.
Trusselsvurdering
Terrorism in the West are most often associated with one of three forms of violent extremism: extreme Islamism, extreme right politics and extreme left politics. The Danish Centre for Prevention of Extremism defines extremism as follows:
Extremism refers to individuals or groups who commit or seek to legitimise violence or other unlawful acts in reference to social conditions with which they are dissatisfied.
The purpose of the threat assessment is to clarify whether your location is a potential attractive terrorist target. Both soft targets – people or crowded places with low security and high accessibility e.g. schools, shopping centres, and public transport – and hard targets e.g. things or buildings, where public access is limited and security is often higher, can be attractive terrorist targets. An attacker will typically aim to harm a large number of people or a target of symbolic importance to gain as much media coverage as possible. However, there have also been cases where the attacks have targeted individuals chosen explicitly by the attacker.
In their "Assessment of the terrorist threat against Denmark (2024)" The Danish Security and Intelligence Service (DSIS) describes the terrorist threat in Denmark in the following way:
“It is the overall assessment of CTA that the terrorist threat to Denmark remains at the level of significant.”
In Denmark and the rest of the world, there have been both thwarted and successful aimed at organisations, crowds, and individuals. The attacks have occurred both in the public domain and at private addresses.
Udendørs offentligt rum
Does your location fit into one of the following categories?
Is the event situated in a larger urban area?
In this context, a larger urban area is defined as either the metropolitan area of a country’s capital city, typically encompassing the central city and its closely linked suburbs. Additionally, other major cities in the country, which are significant urban centers that play key roles in regional or national life.
Are there assets at the location that can be perceived as having symbolic value?
Symbolic value includes e.g. certain population segments (religious and political), cultural assets, and crowded places.
Are there any obviously attractive terrorism targets near the location?
Obvious targets include symbolic targets (religious or political) or crowded places e.g. pedestrian pathways, festivals, public squares, and tourist attractions.
Is there a high density of people at the location during peak periods, daily?
High density is defined as more than 2 people per square meter e.g. at gatherings or events without table arrangements. Peak periods refer to the busiest time of day with the highest number of people at the location.
Is there valuable cultural and/or natural heritage at the location?
Cultural and natural heritage encompasses cultural and natural historical tangible or intangible assets, such as artefacts, UNESCO World Heritage sites, museum pieces, and protected nature. An attack against cultural and natural heritage can contribute to generating media coverage, as well as damaging irreplaceable assets.
Is the location generally well-known and a subject of media coverage?
Generally well-known outdoor public spaces include town squares and pedestrian paths, parks, and waterfronts. Some outdoor public spaces may be the subject of media coverage e.g. tourist attractions, use for public gatherings, or involvement in cases that have attracted media attention.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Perimeter og sikkerhedszone
Perimeteren er den ydre grænseflade af et areal eller en grund, der ofte støder op til nabogrund eller offentligt rum.
Området mellem perimeteren og skallen af bygningen kan anvendes som en sikkerhedszone, der kan forsinke, mindske eller modstå konsekvenserne af en potentiel hændelse.
Is the site's perimeter protected with mechanical security measures?
Perimeter refers to the outer boundary of your property, which can be simply marked or alternatively, physically protected with features such as a fence or wall.
Is there vehicle access control at the site's perimeter?
Access to the area is actively monitored and physically controlled, to prevent vehicles from having unrestricted access.
Is the site's perimeter monitored with electronic security measures?
Perimeter refers to the outer boundary of your property, which you can choose to monitor with e.g. CCTV surveillance.
Have HVM-measures been installed in the site's perimeter?
Hostile Vehicle Mitigation measures, restricting vehicle access and impact include but are not limited to bollards, wedges, reinforced street furniture, trees, or sculptures.
Are the HVM measures certified, or have tests to document the resistance strength been completed?
With a Vehicle Dynamics Assessment (VDA), one can test the resistance strength of e.g. a sculpture or a bench against the specific type of vehicle one wants to protect against.
Can vehicles reach high speed when approaching the site?
High speed can be achieved if there is a long, straight stretch without obstacles, leading to the site. Curbs, ditches, or vegetation can reduce vehicle speed and as a result, any collision impact.
Is the site illuminated?
This refers to external artificial lighting.
Trusselsvurdering
Terrorism in the West are most often associated with one of three forms of violent extremism: extreme Islamism, extreme right politics and extreme left politics. The Danish Centre for Prevention of Extremism defines extremism as follows:
Extremism refers to individuals or groups who commit or seek to legitimise violence or other unlawful acts in reference to social conditions with which they are dissatisfied.
The purpose of the threat assessment is to clarify whether your location is a potential attractive terrorist target. Both soft targets – people or crowded places with low security and high accessibility e.g. schools, shopping centres, and public transport – and hard targets e.g. things or buildings, where public access is limited and security is often higher, can be attractive terrorist targets. An attacker will typically aim to harm a large number of people or a target of symbolic importance to gain as much media coverage as possible. However, there have also been cases where the attacks have targeted individuals chosen explicitly by the attacker.
In their "Assessment of the terrorist threat against Denmark (2024)" The Danish Security and Intelligence Service (DSIS) describes the terrorist threat in Denmark in the following way:
“It is the overall assessment of CTA that the terrorist threat to Denmark remains at the level of significant.”
In Denmark and the rest of the world, there have been both thwarted and successful aimed at organisations, crowds, and individuals. The attacks have occurred both in the public domain and at private addresses.
Ingen af ovenstående
Does your location fit into one of the following categories?
Are there assets at the location that can be perceived as having symbolic value?
Symbolic value includes e.g. certain population segments (religious and political), cultural assets, and crowded places.
Are there any obviously attractive terrorism targets near the location?
Obvious targets include symbolic targets (religious or political) or crowded places e.g. pedestrian pathways, festivals, public squares, and tourist attractions.
Is the location situated in a larger urban area?
In this context, a larger urban area is defined as either the metropolitan area of a country’s capital city, typically encompassing the central city and its closely linked suburbs. Additionally, other major cities in the country, which are significant urban centers that play key roles in regional or national life.
Is there a high density of people at the location during peak periods, daily?
High density is defined as more than 2 people per square meter e.g. at gatherings or events without table arrangements. Peak periods refer to the busiest time of day with the highest number of people at the location.
Is the location generally well-known and a subject of media coverage?
Generally well-known outdoor public spaces include town squares and pedestrian paths, parks, and waterfronts. Some outdoor public spaces may be the subject of media coverage e.g. tourist attractions, use for public gatherings, or involvement in cases that have attracted media attention.
Is there valuable cultural and/or natural heritage at the location?
Cultural and natural heritage encompasses cultural and natural historical tangible or intangible assets, such as artefacts, UNESCO World Heritage sites, museum pieces, and protected nature. An attack against cultural and natural heritage can contribute to generating media coverage, as well as damaging irreplaceable assets.
Er lokaliteten let tilgængelig for en angriber?
Let tilgængelige lokaliteter er ofte nemme at komme ind i uden at blive kontrolleret. En let tilgængelig lokalitethar generelt ingen registrering eller kropsvisitering. Dette kan skyldes lokalitetens funktion eller fravalg af sikkerhedsløsninger.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Perimeter og sikkerhedszone
Perimeteren er den ydre grænseflade af et areal eller en grund, der ofte støder op til nabogrund eller offentligt rum.
Området mellem perimeteren og skallen af bygningen kan anvendes som en sikkerhedszone, der kan forsinke, mindske eller modstå konsekvenserne af en potentiel hændelse.
Is the site's perimeter protected with mechanical security measures?
Perimeter refers to the outer boundary of your property, which can be simply marked or alternatively, physically protected with features such as a fence or wall.
Is there vehicle access control at the site's perimeter?
Access to the area is actively monitored and physically controlled, to prevent vehicles from having unrestricted access.
Is the site's perimeter monitored with electronic security measures?
Perimeter refers to the outer boundary of your property, which you can choose to monitor with e.g. CCTV surveillance.
Have HVM-measures been installed in the site's perimeter?
Hostile Vehicle Mitigation measures, restricting vehicle access and impact include but are not limited to bollards, wedges, reinforced street furniture, trees, or sculptures.
Are the HVM measures certified, or have tests to document the resistance strength been completed?
With a Vehicle Dynamics Assessment (VDA), one can test the resistance strength of e.g. a sculpture or a bench against the specific type of vehicle one wants to protect against.
Kan køretøjer opnå høj fart på vej mod lokaliteten?
Høj fart kan opnås, hvis en lang lige vej fører op til lokaliteten uden forhindringer. Kantsten, kløfter eller bevoksning kan reducere farten for køretøjer og dermed virke skadesreducerende.
Kan der forekomme større køer i nærheden af indgangen til lokaliteten?
Større køer kan forekomme, hvis lokalitet f.eks. bruges til arrangementer. Hvis befolkningsmængder samles uden for lokaliteten køretøjsforanstaltninger, vil det øge risikoen ved et køretøjsanslag.
Er der afstand mellem lokaliteten og det offentlige rum?
Afstand mellem arrangementet og det offentlige rum kan reducere effekten af et potentielt anslag.
Er lokaliteten oplyst?
Dette henviser til udvendig kunstig belysning.
Markerer skilte tydeligt at lokaliteten ikke må tilgås af uvedkommende, eller at der er installeret sikringsforanstaltninger.
F.eks. TV-overvågning.
Er der tilknyttet en vagtfunktion til lokaliteten?
Runderende vagter udfører dynamiske opgaver af forskellig karakter på forskellige tidspunkter og ruter i hele eller dele af bygningen.
Stationære vagter udfører ofte opgaver i forbindelse med faste rutiner, f.eks. en reception- eller portvagt.
Patruljerende vagter udfører ofte udkørende opgaver og tilkaldes efter behov.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Skal, Sektion og Celle
Skallen er en bygnings ydre grænseflade – ofte ydermuren.
Selve bygningen kan sektionsopdeles, så sektionerne sikres med forskellige sikkerhedsniveauer.
Bygningsceller er ofte mindre lokaler i en bygning, der er særskilt sikret.
Er lokaliteten udvendigt overvåget med elektroniske sikringsforanstaltninger?
Med elektronisk overvågning menes f.eks. TV-overvågning, Automatisk Indbrudsalarm, mv.
Er lokalitetens døre, vinduer og glasfacader forstærket med f.eks. sikringsdøre og -glas, sikringsfilm mv.
Ballistiske anslag henviser til brug af skydevåben.
Er der adgangskontrol ved indgangen til lokaliteten for alle brugere?
Adgangskontrol dækker over f.eks. ringklokke til receptionen, elektronisk adgangsbrik eller kort. Brugere betyder både personale og gæster.
Kan en person tilgå lokaliteten gennem alternative passager eller forsyningsveje?
Alternative passager eller forsyningsveje dækker over alle andre indgang end døre og vinduer og kan f.eks. være hegn, kloaksystemer, vandafstrømning eller andre korridorer
Er lokalitetens luftveje og ventilation sikret?
En bygnings ventilation kan sikres, så der kan lukkes for luftstrømmen.
Er lokalitetens forsyning sikret mod afbrydelser?
Forsyning er f.eks. el, gas, internet og telekommunikation, der er nødvendige for at opretholde drift eller vigtige funktioner. Med sikret forsyning menes etablering af nødforsyning eller beskyttende sikringsforanstaltninger.
Kan lokalitetens kritiske aktiver, observeres fra gadeplan eller tilstødende bygninger?
Kritiske aktiver refererer til f.eks. medarbejdere og symbolske mål der ønskes særligt beskyttet.
Gøres der brug af adgangskontrolleret sektionering på lokaliteten?
Sektionering er en opdeling af bygningen, hvor man sikrer bestemte sektioner ved f.eks. skærpet adgangskontrol med bemandet reception, eller at man skal bruge en elektronisk adgangsbrik eller kort, for at kunne bevæge sig rundt mellem dele af bygningen.
Er der etableret tilflugtsrum/-områder på lokaliteten, der kan modstå indtrængning?
Modstandsklassen RC (Resistance Class) definerer modstandstiden mod indbrud i henhold til en specificeret standard.
Sårbarhedsvurdering
The purpose of the vulnerability assessment is to evaluate any vulnerabilities at the site. A vulnerability is any weakness that an attacker can exploit, to make a site susceptible to damage. This should be seen in relation to the assets one wishes to protect and an assessment of the existing threat landscape.
Visible vulnerabilities such as an absence of security measures, can make the site a more attractive target. A good security solution can also reduce the impact of an attack by e.g. limiting the movement of an attacker or providing self-help to people on site.
The questions in the vulnerability assessment are tailored to your initial choice of either outdoor public space, building, or event. Questions will be asked about both physical security measures and security solutions such as emergency management planning and security culture.
Sikkerhedskultur
Sikkerhedskultur handler om, hvordan organisationen og medarbejderne opfatter og behandler risici og ulykker/hændelser. Der findes både gode og dårlige eksempler på sikkerhedskultur, men i alle tilfælde bør organisationer bestræbe sig på at opnå en god og styrket sikkerhedskultur, hvor medarbejderne føler, at det er sikkert at gå på arbejde hver dag.
Har I en sikkerhedsprocedure for åbning af post og pakker?
Dette refererer til hvor, hvornår og hvordan post og pakker bliver modtaget og åbnet.
Har I sikkerhedsprocedurer til identifikation og validering af eksterne personer der vil ind på lokaliteten?
Eksterne personer kan f.eks. være bude der kommer med mad, blomster og post/pakker, vareleverandører, besøgende gæster eller kunder, eller håndværkere.
Har I sikkerhedsprocedurer til rekruttering?
Baggrundscheck kan variere i omfang, men her menes der som minimum at man har modtaget en straffeattest og fulgt op på mindst tre referencer.
Har I en procedure til identificering og håndtering af mistænkelige objekter?
Efterladte genstande som f.eks. tasker og pakker der gør sig bemærket ved deres tilstedeværelse.
Arbejdes der med sikkerhedskultur i organisationen?
Hvordan organisationen og dens medarbejdere opfatter og behandler risici og emner f.eks. risikoperception, awareness og informationssikkerhed.
Arbejdes der med beredskabsplanlægning og foreligger der en beredskabsplan?
I beredskabsplanlægning arbejder man blandt andet med at forebygge de hændelser, som ligger ud over den daglige drift, altså før fasen. Det betyder, at man – gennem uddannelse, træning og planlægning – styrker sin robusthed til at stå imod hændelser, der kan true organisationens kritiske processer.
Er bygningens flugtveje velkendte for bygningens brugere?
Personer der bruger bygningen dagligt er f.eks. personale, rengøringsfolk.
Afholder I beredskabsøvelser?
Beredskabsøvelsen kan f.eks. være en evakueringsøvelse for at afprøve den eksisterende plan med henblik på at teste, om den fungerer efter hensigten.
Er der etableret krisestyring med tilhørende rolle- og ansvarsfordelingmv.?
Når en hændelse udvikler sig til et punkt hvor beredskabsplanlægningen ikke længere kan håndtere den, overgår det til krisestyring.
DIT RESULTAT
Dine svar indikerer et meget begrænset risikobillede og dermed et meget begrænset behov for yderligere terrorsikring af din lokalitet. Da risikoværktøjet er et generisk værktøj, bør du altid søge uvildig rådgivning hos en sikkerhedsrådgiver, der tager højde for din kontekst.
Resultatet er et øjebliksbillede, der påvirkes i takt med centrale ændringer på lokaliteten, eller ændringer i PET’s Vurdering af terrortruslen mod Danmark. Hvis du får nye værdifulde aktiver at beskytte, eller din sårbarhed ændres som følge af ændringer i sikringstiltag, anbefales det, at du tager testen igen.
Du kan nu læse mere om de terrorsikringstiltag, der kan styrke din lokalitets beskyttelse mod terroranslag, ved at trykke på billederne med tiltag nedenfor. De tiltag du får vist nedenfor, er baseret på dine svar i risikoværktøjet. Husk, at du altid kan læse mere om tiltag i vidensbanken.
Dine svar indikerer et begrænset risikobillede og dermed et begrænset behov for yderligere terrorsikring af din lokalitet. Da risikoværktøjet er et generisk værktøj, bør du altid søge uvildig rådgivning hos en sikkerhedsrådgiver, der tager højde for din kontekst.
Resultatet er et øjebliksbillede, der påvirkes i takt med centrale ændringer på lokaliteten, eller ændringer i PET’s Vurdering af terrortruslen mod Danmark. Hvis du får nye værdifulde aktiver at beskytte, eller din sårbarhed ændres som følge af ændringer i sikringstiltag, anbefales det, at du tager testen igen.
Du kan nu læse mere om de terrorsikringstiltag, der kan styrke din lokalitets beskyttelse mod terroranslag, ved at trykke på billederne med tiltag nedenfor. De tiltag du får vist nedenfor, er baseret på dine svar i risikoværktøjet. Husk, at du altid kan læse mere om tiltag i vidensbanken.
Dine svar indikerer et generelt risikobillede og dermed et generelt behov for yderligere terrorsikring af din lokalitet. Da risikoværktøjet er et generisk værktøj, bør du altid søge uvildig rådgivning hos en sikkerhedsrådgiver, der tager højde for din kontekst.
Resultatet er et øjebliksbillede, der påvirkes i takt med centrale ændringer på lokaliteten, eller ændringer i PET’s Vurdering af terrortruslen mod Danmark. Hvis du får nye værdifulde aktiver at beskytte, eller din sårbarhed ændres som følge af ændringer i sikringstiltag, anbefales det, at du tager testen igen.
Du kan nu læse mere om de terrorsikringstiltag, der kan styrke din lokalitets beskyttelse mod terroranslag, ved at trykke på billederne med tiltag nedenfor. De tiltag du får vist nedenfor, er baseret på dine svar i risikoværktøjet. Husk, at du altid kan læse mere om tiltag i vidensbanken.
Dine svar indikerer et alvorligt risikobillede og dermed et alvorligt behov for yderligere terrorsikring af din lokalitet. Da risikoværktøjet er et generisk værktøj, bør du altid søge uvildig rådgivning hos en sikkerhedsrådgiver, der tager højde for din kontekst.
Resultatet er et øjebliksbillede, der påvirkes i takt med centrale ændringer på lokaliteten, eller ændringer i PET’s Vurdering af terrortruslen mod Danmark. Hvis du får nye værdifulde aktiver at beskytte, eller din sårbarhed ændres som følge af ændringer i sikringstiltag, anbefales det, at du tager testen igen.
Du kan nu læse mere om de terrorsikringstiltag, der kan styrke din lokalitets beskyttelse mod terroranslag, ved at trykke på billederne med tiltag nedenfor. De tiltag du får vist nedenfor, er baseret på dine svar i risikoværktøjet. Husk, at du altid kan læse mere om tiltag i vidensbanken.
Dine svar indikerer et meget alvorligt risikobillede og dermed et meget alvorligt behov for yderligere terrorsikring af din lokalitet. Da risikoværktøjet er et generisk værktøj, bør du altid søge uvildig rådgivning hos en sikkerhedsrådgiver, der tager højde for din kontekst.
Resultatet er et øjebliksbillede, der påvirkes i takt med centrale ændringer på lokaliteten, eller ændringer i PET’s Vurdering af terrortruslen mod Danmark. Hvis du får nye værdifulde aktiver at beskytte, eller din sårbarhed ændres som følge af ændringer i sikringstiltag, anbefales det, at du tager testen igen.
Du kan nu læse mere om de terrorsikringstiltag, der kan styrke din lokalitets beskyttelse mod terroranslag, ved at trykke på billederne med tiltag nedenfor. De tiltag du får vist nedenfor, er baseret på dine svar i risikoværktøjet. Husk, at du altid kan læse mere om tiltag i vidensbanken.